Pen-Tests
Test Plan – Stages
The following stages may vary slightly, this is dependent on the designated scope, limits and extents set by the client for the subject Penetration Tests to be performed on the systems. Since no specific criteria has been set by the client, a standard method will be followed, testing stages have been aligned to the industry best practises to ensure a quality standard is established.
Stage 1 – Reconnaissance
Information is gathered about the target without engaging any type of attack. Information can be gathered, but not limited to, search engines, information harvesters, social media or social engineering. This stage of the Pen-test is setting the scenario for possible attack vectors to be identified.
Searching for information is completed using active and passive approaches. The active method engages directly with the target, an example would be browsing the subject company’s website for any sensitive information or systems/software being used, however this approach may give an alert of the attacking machines identification. Passive reconnaissance uses readily available information on the internet but no interaction with the subject target is made.
General Mitigation:
Both target machines in this report are vulnerable web servers and therefore the mitigation methods that should be considered are re-configuration of the web servers and limiting the amount of data available on the website. Other mitigation methods include Disabling the web server directory listings, encrypt sensitive information and include password protection with best practise guidelines.
Stage 2 – Scanning
The scanning phase is used to gain further information about a target. The information returned from the scans should be sufficient enough to provide detailed services and web server structure.
Scanning provides the basis of information for the next stages of testing, the information returned should provide detailed information regarding the network structure, resources, components available and systems Banner info.
Types of scans that are normally subjected to the target at this test stage are Port scans, Network scans and Vulnerability scans.
Port scans send specially created data packets to a target machine to return information about the services and open ports that are available. Industry standard is to use NMAP for this type of activity.
Network Scans can be used to build detailed information of endpoints and hosts on a network. Once mapping has been completed specific targets can be singled out for detailed deeper probing. This type of activity involves running a ping sweep across a range of IP’s to determine if the IP is in use by a machine.
Vulnerability scans are used to identify if a specific target has weaknesses or vulnerabilities that can be exploited. These scans are normally formed into a legible report which will be studied in detail for potential attack vectors formation.
The characteristics of this stage depends entirely on the type of testing that is required by the client, systems, hosts, network, infrastructure, web servers, social engineering etc.. In this report a general overview of the target’s main webservers security configuration issues are investigated. In other circumstances there is the possibility that a complete security evaluation of the targets is required, in that instance additional testing is required.
General Mitigation:
Possible mitigation involves the inclusion of Firewalls, Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) on the network to block, restrict or alert to abnormal activity. Blocking of specific protocol types, for example Internet Control Message Protocol (ICMP). Ensure all Operating systems and firmware have been updated accordingly. Services that are not being used should be disabled or appropriately hardened. Banners can be disabled if not critical for the network advertisement.
Stage 3 – Enumeration
Enumeration is key to building information about the target credentials, groups, hostnames and services running. This type of activity directly engages with the target to gather critical information via direct requests. There are various methods for extracting or discovering the information, brute forcing services with dictionary wordlists, or building usernames from emails for testing against databases. The type of method applied will vary depending on the designated application being attacked.
Enumeration has the potential to return vast amounts of information from the target, the tools, programs and techniques used will be connecting actively to the target system. Attack detection risk is high during this stage so the attacks must be planned and executed accordingly.
Investigation during this stage returns more than sufficient detail, it is now considered as passing the limits on how much knowledge of the systems which has been returned is not legal. This stage is explored when further systems access is required. At this stage it is important to acknowledge the types or vulnerabilities found, these should be documented in detail with Industry proven countermeasures to protect against the subjected attacks. Special attention and care must be taken while executing tests during this stage, some of the tools exercised have the potential to disable the system or even an entire network. At this point a high value target list can be identified and prepared for the next phase.
General Mitigation:
Configure the services correctly or block the ports. Ensure no default manufactures credentials are used, these must be changed before the services go live. Apply account lock-out, maximum tries and service time-outs if logins are attempted too frequently. Ensure that information about the equipment, e.g. email server info, is not included in the email communications. Restrict sharing of folders, services and equipment to an essential basis only.
Stage 4 – Exploitation (System Hacking)
Providing sufficient vulnerable vectors have been identified in the previous stages investigations, attacks can be launched to attempt to gain system access. In most cases several attacks can be launched at different vulnerable services to ensure that at least one is successful.
The exploitation phase subjects attacks on systems to gain explicit access to the services, resources and files by bypassing the security or taking advantage of insecure services. Specific attacks are engaged and directed at the vulnerable services to establish open connections and backdoors to the systems. The attacks are particularly focused on areas that contain valuable assets of the target machine.
This report has taken into consideration some of the most explicit vulnerabilities accessible on the subject test machines. Direct logins via commercially used administration ports and backdoors are created following standard procedures and referenced to Exploit Databases. Other types of attacks include brute forcing discovery of credentials, traffic analysis for proof of ports use and data transfer via specific ports.
General Mitigation:
Mitigation here is an overall complete security aspect of the host systems and network. All aspects of securing the systems must be taken into consideration, web application security, Encoding, Anti-Virus, Encryption and Web Application firewalls should be present. Not only should all of the fore mentioned mechanisms be applied during the live application of the system but also implementation of the system security design must be considered during the development phase. Best practises for network and system configurations, credentials, port hardening and data sharing must be adhered to. Human interventions are also key features to be taken into consideration, continuous training should be provided for company staff to inform them of the threats related to these types of security issues as well as social aspects.
Stage 5 – Post Exploitation
This is effectively a clean up phase and reporting element of the Pen-Test. In this stage several additional activities are performed, all remote connections must be closed and returned to the original state as well as closing any purposely opened ports. Log files corresponding to the unauthorised logins and tests should be wiped accordingly. In the account of subjecting the target systems to extensive testing with possible systems security disarming, returning the systems to the original state ensure that no responsibility for the contractor is sort after in case of compromise after testing has been finalised.
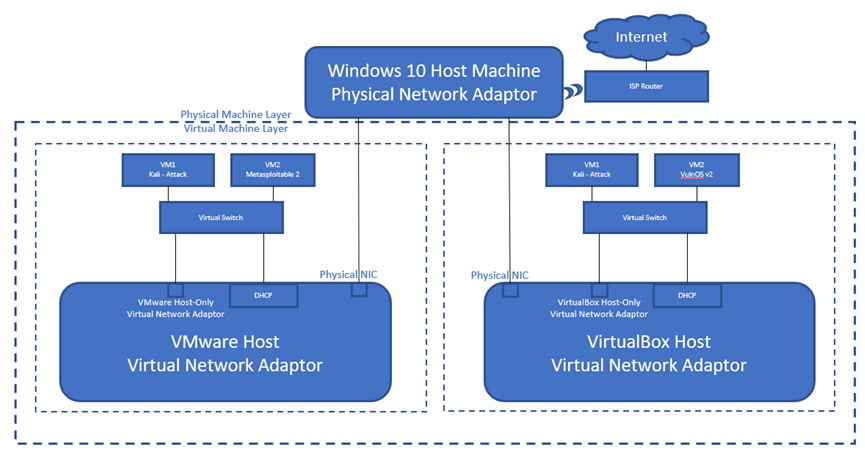
Vulnerable Machine Walkthroughs
| Metasploitable 2 Walkthrough | https://charlesmarrow.uk/index.php/pen-tests/metasploitable-2/ |
| VulnOSv2 Walkthrough | https://charlesmarrow.uk/index.php/pen-tests/vulnosv2/ |