Research Projects
- Network Vulnerability Traige Tool (Project Completed)
- Threat Modelling of Personal Mobile/End Devices – Geo-location, Privacy, User/Attacker Interaction (In progress)
- Low Latency Induced Network Security Implications (Early Stages)
- Cyber Malware Threat Hunting Using an ESXI Virtual Environment
- Network Vulnerability Traige Tool
Introduction
Recent implications and obligatory remote working draw attention towards workers using more cooperate equipment and IOT devices in the confinements of their own home. The necessary security mechanisms and software may not be present and therefore pose a direct risk of unauthorised access to businesses data and services. There is a very real requirement to conduct security testing on Smart Home, Home Offices and Small Business networks. Network and device security weaknesses can be expored by non-technical IT users eabling them to interpret the vulnerabilities corresponding to the subject test network.
Figure i shows the basic project concept in block form for a simplifed representation.
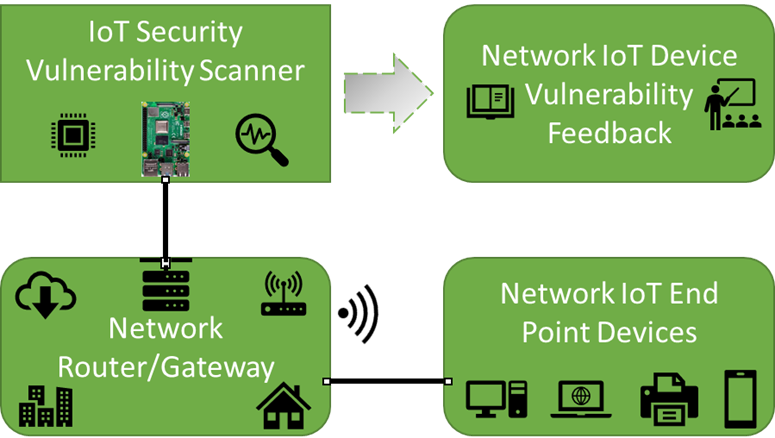
Theoretical Process
- Scanner waits for an Ethernet connection Before initiating the automated scans.
- Automated scans run in a dedicated order, convert results and store them in a webserver folder.
- Automated Vulnerability scans execute and compare results against a vulnerability online database, results are then converted and stored on the webserver folder.
- Results can be viewed via a web browser by accessing the IoT Vulnerability scanners IP address.
General Design
Preliminary design of the Tool has been developed using a virtualised version of Kali Linux connected to the subject network testbed with only select known devices. The initial preparation for the semi-automation has been chosen via this method to avoid upload and program modifications on the host device, this has saved valuable time with the project schedule. Using a standard version of the operating system ensures that the preliminary results are justifiable and relevant for the main development phase.
Once positive results had been gathered and the scripts are producing the expected results as per the design, the main automated program is incorporated into the subject host test device running a micro version of Kali Linux.
Tools, Special functions and devices
nmap > Live host search and store, XML nmap and gnmap file creating
Bash Script > Ethernet live connection, Sleep, wait, XML to html convertion
Crontab > startup bash scritpts at instance in the program iniciation
Apache2 Webserver > Storage and veiwing of results
Testbed Devices > Various IoT and computer devices
Results Examples
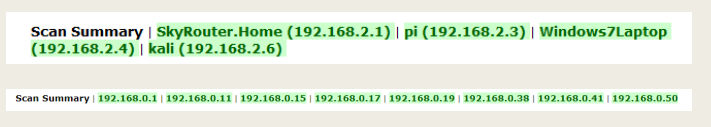
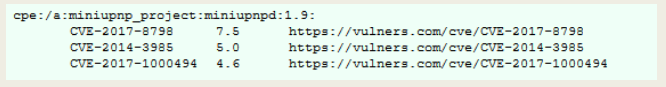
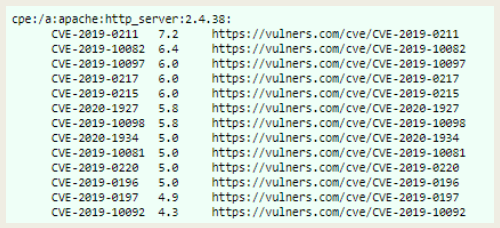
Final Reflection
Even though standard industry tools have been used and implemented together the tool provides a justifible reflection of the vulnerbilities existing on a network. The scope and aim proves that network threats can be explored and presented in a legible format even for a novice IT user. The tool is completely automated ensuring that no expert skill IT level is required. All tools are open source justifying and promoting a zero cost effective solution.
For details on the scripts used, further information on the automated scanning process or just being inquisitive please click contacts to get in touch
2. Threat Modelling of Personal Mobile/End Devices – Geo-location, Privacy, User/Attacker Interaction
Introduction
Many instances of vulnerable people are now increasingly having thier personal IT space infiltrated. The main purpose of this project is build a threat vs mitigation data base to help protect vulnerable people and support a better quality of life.
Scope
Generate a data base corresponding to typical and real threats that could affect a vulernable person, including but not limited to the following design points:
- Geo-location on Mobiles and PC’s
Many devices have multiple applications tracking the location: maps, social media, other applications - Unauthorised Account Access or Admin Accounts
Attacker with unauthorised access to accounts could access sensative data or important information - Smart Speakers
Smart speakers can be remotely accessed and conversations recorded without prior permission or rights - Smart TV’s
Possibility of spying remotely via a Smart TV’s webcam enabled device - Vulnerable Person Social Engineering
Scared or worried victims are easily led into a security assurance from an attacker and therefore system comprimised
Once the data base has been generated with respect to the threat conditions, mitigation examples can be matched as well as direct instuctions on how to mitigate these security gaps and add an ever increasingly import layer of protection – piece of mind.
Use specific industry standard texts and best practices to form the database, e.g. BS, NIST, Secure by design, etc.
Expected Outcome
Clients are able to select generic devices or operating systems against type of threat and will be presented with mitigation examples. Mitigation examples will be in the form of a procedure or set of instructional videos.
¬Project in Progress
For details on project design and scope or just being inquisitive please click contacts to get in touch
3. Low Latency Induced Network Security Implications
Introduction
Demand and supply, speed and network bandwidth equal greater revenue providing the conditions can be satisfied. Web-Services require rapid depolyment and continuous maintenance but will result in service disruption. There are several interesting aspects of low-latency networks that reduce the overall security of the network, data in transit and static data. Methods like shortest path/route, reduced encryption, prefetching via DNS lookups or fewer HTTP requests can be implimeted. Low lantency methods are to be investigated in detail for relevant security issues.
Research the security implications of Low-Latency web-service structures and routing methods.
¬Project in progress
For details on project design and scope or just being inquisitive please click contacts to get in touch